-
-

Protect yourself from WordPress User Enumeration Attacks and how to prevent it.
So what is user Enumeration Attacks?
Well user Enumeration Attacks are several brute-force techniques with the purpose of guessing or confirming login credentials such as usernames, e-mail addresses and passwords. Basically a hacker attempts to guess your login information and they do not of course do this manually but they use computers/servers to randomly scan the internet with bot spiders to din a vulnerable website; you website!
User enumeration is often a web application vulnerability, though it can also be found in any system that requires user authentication. Two of the most common areas where user enumeration occurs are in a site’s login page and its ‘Forgot Password’ functionality.
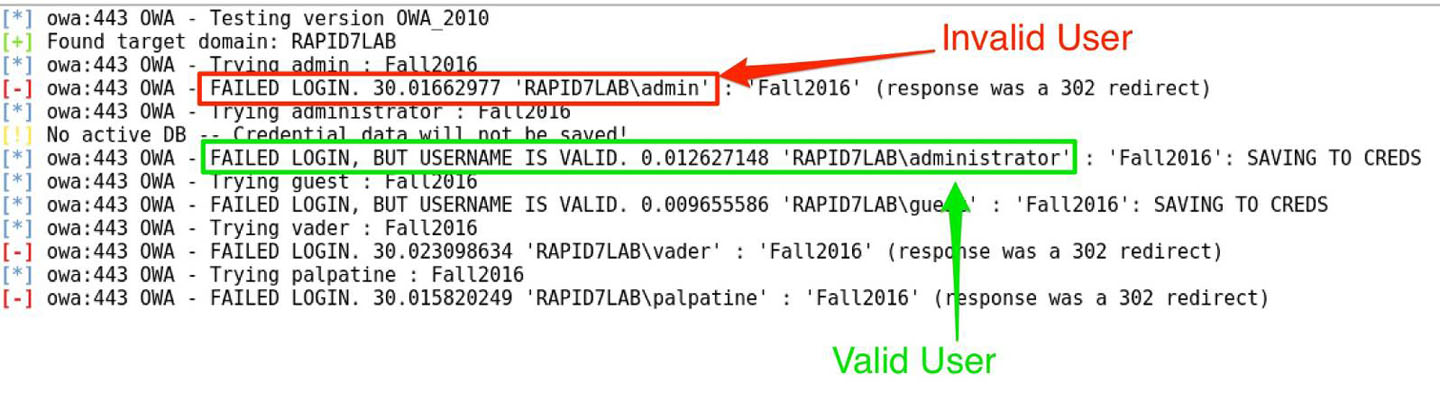
The malicious actor is looking for differences in the server’s response based on the validity of submitted credentials. The Login form is a common location for this type of behavior. When the user enters an invalid username and password, the server returns a response saying that user ‘rapid7′ does not exist.
By default, WordPress is vulnerable to such User Enumeration attempts. Of course, bad username and password practices will have an even greater impact on this vulnerability.
The two most common web application targets for enumeration attacks are:
- The login page
- Password reset page
A webserver with poor application security will identify a non-existent username with an invalid username message where is displays that either the user name does not exist or password is incorrect:

This confirms for a hacker/ cyber criminal that the user/password doesn’t exist in the database. Thus this is a way to validate if the user does not exist and keep trying until a combination works and the hacker can successfully login.

How Does User Enumeration Work in WordPress?
Method 1: Author Archives
Perhaps the easiest method to find WordPress usernames is by going through the author archives. To enumerate usernames through the author archives method, simply append an integer (i.e. 1,2,3, etc.) as a value to the parameter “author”. For example, look at the following values:<codestyle=”color:#000000;”>http://example.com/?author=1 http://example.com/?author=2 http://example.com/?author=3
These values would then fetch the results like the following:
http://example.com/author/admin/
http://example.com/author/user2/
http://example.com/author/user3/Therefore, by fuzzing the parameter author in the WordPress home URL, multiple author names can be enumerated.
How can you prevent these attacks?
Use a security plugin such as :
- WPMU Dev Defender – https://wpmudev.com/project/wp-defender/
- CledanTalk Cloud firewall: https://cleantalk.org/wordpress-security-malware-firewall
- WordFence – https://wordpress.org/plugins/wordfence/
- All-In-One Security (AIOS) – https://wordpress.org/plugins/all-in-one-wp-security-and-firewall/
- BBQ Firewall – https://wordpress.org/plugins/block-bad-queries/
- Really Simple SSL (Their pro version which allows you to lock down vulnerabilities): https://wordpress.org/plugins/really-simple-ssl/
- Require two-factor authentication (2FA) on all users on your website. At least for the administrators, editor and moderation accounts.
- Use strong password that is at least 15-20 characters long and mixed with both upper, lower characters and various symbols. You could use for this purpose a password manager such as Lastpass: https://www.lastpass.com either for yourself or your entire team and set the password policies there too. This will prevent any hackers from finding any weak passwords in your website. LastPass can also generate passwords up to 100 characters making passwords extremely secure.
You can also do further hardening of your WordPress security by blocking user-enumeration through functions.php in your WordPress theme:
Alternatively you could also do it by creating a WordPress MU-plugin:
A MU-plugin is a little custom code plugin that enables the code’s function systemwide. This is very useful and requires a less resources from your servers too than using a plugin for it. It also is beneficial when running WordPress Multisite as all websites created in the system will apply the code simultaneously thus effectively protecting all websites instead of manually applying it to every website’s theme functions.php.
How to activate your MU-plugin:
Once you saved the plugin with a unique name “My-plugin-function.php“.
Now create a new directory in your WordPress installation server folder E.g. the www folder:Save or create your MU-plugin folder as follows: Path: Your www root folder >>> wp-content >>> mu-plugins
and upload your new MU-plugin to that folder. Once it is uploaded it is activated instantly. That’s it!
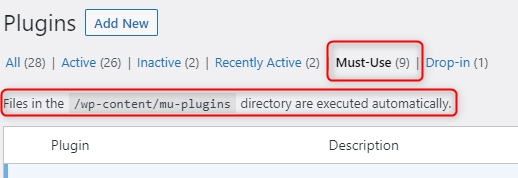
You can confirm also that the MU-plugin is activated:
Login to your WordPress admin back-end and click on “plugins” in the right menu pane. Click on “Must Use” and find your new mu-plugin in the list.

Block WordPress Enumeration through the .htaccess file:
You can also block at server level rather than website level and block server requests by adding the this .htaccess code in your server’s www root.
Note: You must change http://mywebsite.com to your own website domain name address!span
Examples of Complex Enumeration Attacks:
LDAP Enumeration: Light-Weight Directory Access Protocol (LDAP) is a protocol used to access directory services – hierarchical structures of user records.
A successful LDAP enumeration attack could reveal the following sensitive information:
- Usernames
- Addresses
- Contact information
- Business sector information
NetBIOS Enumeration
Network Basic Input Output System (NetBIOS) is used as an API that enables endpoints to access LAN resources.Each NetBIOS protocol is comprised of a unique 16-character string that identifies network devices over TCP/IP.
To facilitate NetBIOS enumeration attacks, printer and file services need to be enabled. These attacks occur via port 139 on the Microsoft Operating System.
A successful NetBIOS enumeration attack could make the following attacks possible on the compromised machine.
- The compromised endpoint could be recruited into a Botnet and used to launch DDoS attacks.
- The hackers could execute further enumerate privileged access accounts to gain access to sensitive resources.
- SNMP Enumeration
Simple Network Management Protocol (SNMP) is a framework for requesting or modifying information on networked devices. SNMP is software agnostic, meaning networked devices can access regardless of the type of software they are running.
Cyberattacks enumerate SNMP on remote devices to gather the following intelligence:
- Traffic behavior
- Remote device identifiers
- Identifying information about networked devices and resources
An angel in wolves clothing..
-
Good and useful information.
Thank you for nice write up Angelus. 👍 -
-
You must be logged in to reply to this topic.